 Weird Stuff
Weird Stuff  Weird Stuff
Weird Stuff  Mysteries
Mysteries 10 Tragic Disappearances and Deaths in Joshua Tree National Park
 History
History 10 Ways Childhood Really Sucked in the Old West
 Music
Music 10 Name Origins of Famous Bands from the 1990s
 Religion
Religion 10 Biggest Turnarounds by the Catholic Church
 Weird Stuff
Weird Stuff 10 Unbelievable Times Laws Had Unintended Consequences
 Humans
Humans Ten Historic Women Who Deserve Way More Credit Than They Got
 Movies and TV
Movies and TV 10 Films That Spawned Major Lawsuits
 History
History Ten Times Towns Were Wiped Off the Face of the Earth
 Creepy
Creepy 10 of the Most Disturbingly Haunted Public Houses in the UK
 Weird Stuff
Weird Stuff 10 Niche Subcultures That Are More Popular Than You Might Think
 Mysteries
Mysteries 10 Tragic Disappearances and Deaths in Joshua Tree National Park
 History
History 10 Ways Childhood Really Sucked in the Old West
Who's Behind Listverse?

Jamie Frater
Head Editor
Jamie founded Listverse due to an insatiable desire to share fascinating, obscure, and bizarre facts. He has been a guest speaker on numerous national radio and television stations and is a five time published author.
More About Us Music
Music 10 Name Origins of Famous Bands from the 1990s
 Religion
Religion 10 Biggest Turnarounds by the Catholic Church
 Weird Stuff
Weird Stuff 10 Unbelievable Times Laws Had Unintended Consequences
 Humans
Humans Ten Historic Women Who Deserve Way More Credit Than They Got
 Movies and TV
Movies and TV 10 Films That Spawned Major Lawsuits
 History
History Ten Times Towns Were Wiped Off the Face of the Earth
 Creepy
Creepy 10 of the Most Disturbingly Haunted Public Houses in the UK
Top 10 Most Catastrophic Computer Failures In History
We rely on computers for an ever-increasing proportion of our day-to-day lives. As such, it can sometimes be hard to imagine how something so common and well-understood could ever lead to errors costing hundreds of millions or even billions of dollars.
Nevertheless, severe security flaws affect almost every single device on the planet (yes, likely including the one you’re reading this on right now), and rushed designs can claim hundreds of lives. Let’s take a look at ten times computers failed—or were made to fail—in expensive, sometimes even deadly, ways.
10 Mars Climate Orbiter

The Mars Climate Orbiter was a small space probe launched on December 11, 1998, by NASA to enter Martian orbit and both study the atmosphere of the Red Planet and provide valuable insight into its climate and any surface changes that might occur. The launch went as planned, and the probe traveled toward Mars with seemingly no issues, but unknown to the mission control team on Earth, the spacecraft was being put on a trajectory that would lead to the failure of the mission.
The orbiter was being navigated by various teams of people—some who used metric units, and others who used imperial units. Due to this simple conversion error—and the misconfiguration of the computer systems on the part of Lockheed—a course correction sent the Mars Climate Orbiter far too close to the planet, and it was likely violently burned up and destroyed in the atmosphere.[1]
9 Ariane 5
Ariane 5 is a class of heavy-lift space rocket utilized in Europe. Jointly created by 20 European nations—including Belgium, France, Germany, and the United Kingdom—it has been continuously refined and altered to be more efficient, reliable, and powerful and is still in use today.
Following its initial development, the first fully completed Ariane 5 rocket lined up on the launchpad and prepared for its maiden flight on June 4, 1996.[2] The rocket fired up the engines on both its core stage and its gigantic boosters and took to the skies, accelerating upward and beginning to turn at a much greater rate than its predecessor, the Ariane 4, as expected. Unfortunately, this was exactly why the rocket failed.
The internal computers and software responsible for monitoring speed and orientation aboard the Ariane 5 were reused from the Ariane 4, but the greater speed of the new rocket caused the computers to experience a “hardware exception” while converting a 64-bit floating point number to a 16-bit integer. Essentially, the more powerful rocket exceeded the limits of the older systems in just 37 seconds, causing the stored numbers to flip from 32,768 to – 32,768, confusing the rocket and initiating a sudden turn downward that resulted in a catastrophic breakup and aerial explosion, destroying both the rocket and its payload.
8 Knight Capital Group
Knight Capital was a American-based financial services firm buying and sharing stocks of huge value in large quantities on the global stock market. It was the dominant trader in the United States, with a share of approximately 17 percent on NASDAQ.
This all came crashing down at practically a moment’s notice on August 1, 2012.[3] That morning, when the stock market opened, the automated computer systems based at Knight Capital began rapidly buying and selling millions and millions of shares distributed among hundreds of stocks for a total of 45 minutes, before the systems were isolated and stopped. Knight Capital was forced to sell these shares back at low prices, which resulted in a total net loss of over $440 million—or roughly $10 million per minute.
New trading software had been installed improperly on one of the computers by a technician, which caused the fault and destabilized the entire stock market for a short period. Following this debacle, Knight Capital had to be acquired by another financial firm, Getco, as the company simply lacked the money to continue and had to be “rescued” by other firms.
7 Stuxnet

Stuxnet is the name given to a piece of malware discovered in 2010 and thought to have been in joint development by the Americans and the Israelis as a cyberweapon since 2005. Targeting real-world mechanical systems, Stuxnet is generally regarded as the first known piece of malware intended to cause real-world, tangible damage.
Stuxnet appears to have mostly been employed against Iran’s nuclear program—infiltrating the nuclear facility at Natanz and infecting its computer systems, manipulating machinery in a destructive manner. It appears to have been snuck in via a simple, easily detectable USB drive, of all things. Between November 2009 and late January 2010, it is estimated that this malware caused 1,000 nuclear centrifuges—ten percent of the facility’s total number—to violently tear themselves apart by forcing changes in rotor speed.[4] Stuxnet forced the centrifuges to first increase in rotation speed and then decrease in a highly effective attempt to cause instability. It is estimated that this destruction resulted in a 30-percent decrease in nuclear enrichment efficiency for Iran—a huge impact that undoubtedly hindered Iranian nuclear efforts.
6 WannaCry
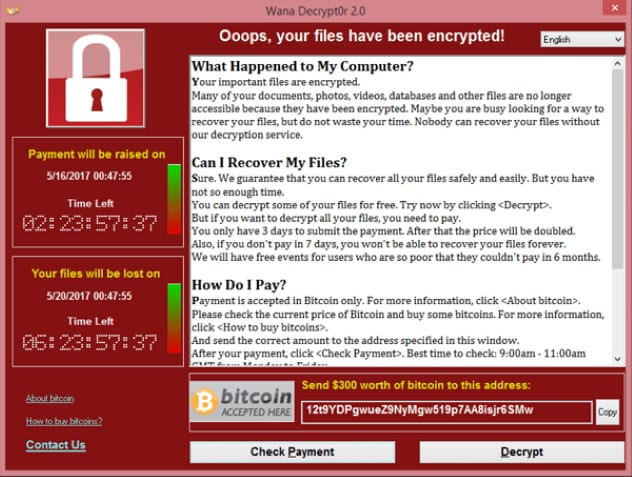
In May 2017, a worldwide cyberattack was launched that infected Windows-based computers with ransomware. Ransomware is a form of malicious software that encrypts user data, making it unusable, and demands a payment to decrypt it and give it back to the user.[5] WannaCry most significantly affected older Windows systems like Windows XP and spread to over 200,000 computers in 150 countries.
The ransom demanded between $300 and $600 per computer. Data was returned safely to those who paid the ransom. The United Kingdom’s National Health Service was especially badly affected, and tens of thousands of computers controlling MRI scanners, theater equipment, and more were attacked, causing some nonemergency cases to be turned away while the attack was contained. Worldwide, the cost is estimated at up to an enormous $4 billion, and the West has placed the blame squarely on North Korea’s shoulders.
5 Dhahran Patriot Missile Interception

The Patriot missile system is a United States-developed surface-to-air missile system capable of shooting down both aircraft and ballistic missiles, should they be detected and confirmed as enemy targets. It is widely employed today by both the United States and several of its allies, including Germany. It was also widely used in the Gulf War of 1991 to protect American soldiers and aircraft, which is where it failed due to a known software error.[6]
A Patriot missile system installed in Dhahran, Saudi Arabia, had been operational for 100 hours, causing its internal clock to drift by 0.34 seconds. The Israelis had detected this issue two weeks earlier and advised the US to periodically reboot the system’s computers. This was not conducted. On February 25, 1991, a “Scud” ballistic missile launched by Iraq hit the US Army barracks in Dhahran, killing 28 American soldiers. The Patriot missile system had activated and detected the missile, predicting where to look for it next—due to the drifting internal clock, the system looked in the wrong place and found no missile, so it shut down and did not attempt an intercept, which could have saved many lives.
4 Meltdown

Meltdown is a vulnerability present in all Intel CPUs released between 1995 and October 2018, as well as some ARM processors. Given that the vast majority of all computers run Intel CPUs, security analysts describe the vulnerability as “catastrophic” and initially didn’t believe the reports of the vulnerability to be true, due to how severe they were.
Meltdown exploits the way modern CPUs function and allows processes running on a computer to see all information currently being used by the CPU by avoiding security measures designed to stop this. The implications of this are terrible—someone using Meltdown to attack a computer could see passwords, sensitive financial information, images, and practically anything they wanted without users’ knowledge, all while avoiding antivirus software.[7] Intel has released emergency security patches to fix this exploit, as has Microsoft, but this has reportedly come at a cost of performance—from five percent to a whopping 30 percent. Given how widespread this exploit is, it is most definitely destructive.
3 Spectre

Spectre is similar in nature to Meltdown. It was also uncovered in 2018, but it’s even more widespread. While Meltdown is only effective against Intel CPUs for the most part, Spectre affects practically every single computer system as of 2019. It has been reported that some variants of Spectre cannot be mitigated to any reasonable degree by software changes at all and will require hardware changes which are currently being implemented.
Spectre works by tricking a program into accessing innocent-seeming memory but actually allowing an attacker to read this data and potentially retrieve sensitive information without user approval.[8] As of this writing, only a very small amount of CPUs are immune to this exploit—most notably the recently released AMD Zen 2 processors and Intel Ice Lake processors. Software patches, like with Meltdown, are applicable but again introduce performance drops comparable to Meltdown, in addition to causing sudden, unexpected reboots as patches are applied. It is unlikely that Spectre will disappear completely for a very long time, until hardware mitigations are employed within every single computer system—and it is likely it is affecting you right now.
2 ILOVEYOU
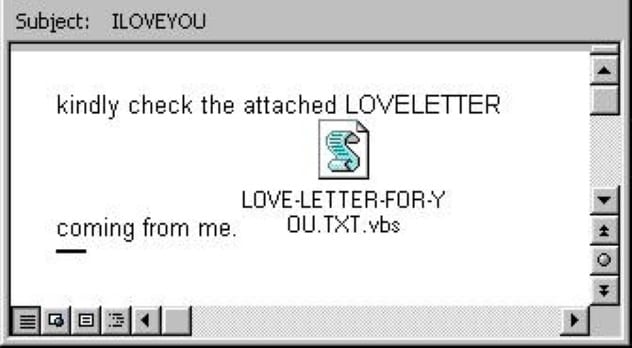
Starting on May, 5, 2000, tens of millions of people around the world received an e-mail with the subject “ILOVEYOU.” The e-mail generally contained a small sentence like “Please read the attached LOVELETTER from me” and would have a file attached. The file was called “LOVE-LETTER-FOR-YOU.TXT.vbs,” and millions of people opened it out of curiosity—perhaps searching for love—causing the script contained within it to activate.[9]
The hidden script would destructively overwrite random files on the computer and automatically send a copy of itself to every single address in Microsoft Outlook, causing it to spread extremely quickly. ILOVEYOU began in the Philippines and spread to Hong Kong, Europe, and finally the US. It is estimated that the malware caused approximately $8 billion in damages worldwide and cost around $15 billion to remove from computer systems. Ten percent of all Internet-connected computers in the world were affected, and 50 million infections were reported in just a span of ten days.
1 Boeing 737 MAX

The Boeing 737 MAX is a variant of the aging Boeing 737 line of narrow-body, twin-engine passenger airliners originally developed in the late 1960s. Since then, the 737 has been routinely updated and upgraded to fit in the modern world of aviation. However, it could be argued that the 737-MAX took this a step too far.
Rushed into development and production, the 737-MAX needed greater efficiency to keep its fuel costs as low as possible. To do this, it needed larger engines that could not be traditionally mounted on its wings. As a workaround, the larger engines were mounted further forward than normal, introducing a number of differences in the way it flies. To avoid the increased cost of pilot retraining for these new characteristics, Boeing instead implemented a system known as MCAS to mitigate these differences by automatically pushing the nose of the aircraft down when excessive angle of attack is detected. It was this software acting erroneously that led to the crash of two 737 MAX flights months apart: Lion Air flight 610 in October 2018 and Ethiopian Airlines flight 302 March 2019, claiming a combined total of 346 lives as the aircraft were forced into the ground by the MCAS system. Since these two crashes, the 737-MAX has been grounded worldwide and is not allowed to fly passengers due to safety concerns.[10]
A guy from London, writing lists on anything he finds interesting—generally something scientific or technology-based.
Read about more memorable computer failures on 10 Times Computers Went Rogue and 10 Seriously Epic Computer Software Bugs.
![Top 10 Most Important Nude Scenes In Movie History [Videos] Top 10 Most Important Nude Scenes In Movie History [Videos]](https://listverse.com/wp-content/uploads/2019/09/sharonstone-150x150.jpg)







