 Mysteries
Mysteries  Mysteries
Mysteries  History
History 10 Surprising Stories About the Texas Rangers
 Humans
Humans 10 Philosophers Who Were Driven Mad by Their Own Theories
 Miscellaneous
Miscellaneous 10 Video-Game-Worthy Weapons and Armors from History
 Weird Stuff
Weird Stuff 10 Psychics Who Accurately Predicted Wartime Events
 The Arts
The Arts 10 Pieces of Art Inspired by a Broken Heart
 Health
Health 10 Science Fiction-Sounding New Medical Treatments
 History
History 10 Surprising Facts About the Father of Submarine Warfare
 Space
Space Ten Astonishing New Insights into Alien Worlds
 Weird Stuff
Weird Stuff 10 Bizarre Summer Solstice Rituals Still Practiced Today
 Mysteries
Mysteries Top 10 Haunting Facts About the Ghost Ship MV Alta
 History
History 10 Surprising Stories About the Texas Rangers
 Humans
Humans 10 Philosophers Who Were Driven Mad by Their Own Theories
Who's Behind Listverse?

Jamie Frater
Head Editor
Jamie founded Listverse due to an insatiable desire to share fascinating, obscure, and bizarre facts. He has been a guest speaker on numerous national radio and television stations and is a five time published author.
More About Us Miscellaneous
Miscellaneous 10 Video-Game-Worthy Weapons and Armors from History
 Weird Stuff
Weird Stuff 10 Psychics Who Accurately Predicted Wartime Events
 The Arts
The Arts 10 Pieces of Art Inspired by a Broken Heart
 Health
Health 10 Science Fiction-Sounding New Medical Treatments
 History
History 10 Surprising Facts About the Father of Submarine Warfare
 Space
Space Ten Astonishing New Insights into Alien Worlds
 Weird Stuff
Weird Stuff 10 Bizarre Summer Solstice Rituals Still Practiced Today
Top 10 Ways You Didn’t Know You Could Get Hacked
Discover the ways that someone might hack your computer, steal your identity, or steal your financial information without you ever knowing it — until it is too late. As you will learn, the best way to defeat a hacker is to understand how they typically hack you. By understanding some of these basic principles while going about your way online, you can make yourself less of a target for the nefarious side of cyberspace — without having to understand all the technical jargon.
10 Times Hackers Hacked Live Television
10 Drive-By Downloads
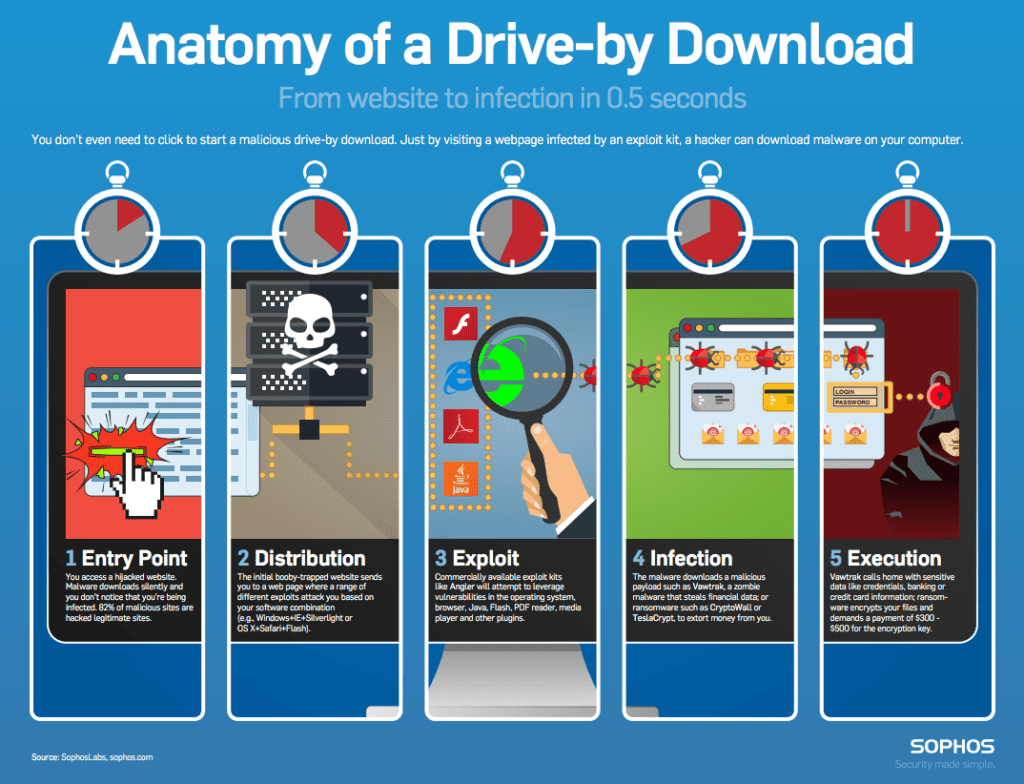
This is a term that sounds scary, and it is, as it can happen when visiting a website that would normally be trustworthy. If you visit a website that has been hacked, it may appear to be acting normal, but it could be secretly scanning your computer or mobile device for known vulnerabilities, installing malicious software through whatever vector it finds, then being able to do pretty much anything. That includes stealing your data, monitoring your behavior, secretly viewing you via your webcam, and more.
If it turns out your device hasn’t been updated or patched recently, malicious software can get installed through a drive-by download attack, allowing a hacker to completely take control of your system. Keep your computer and mobile devices updated, and use current malware/virus protection to stay safe.
9 Cross-Site Scripting (XSS)

A hacker can leverage flaws in a website’s javascript code to compromise the cookies stored in your web browser, which could lead to them stealing your personal information, or even your login credentials to that website and others. In some cases they could even steal the contents of your system clipboard, other website cookies, and usernames/passwords.
Similar to drive-by downloads, this type of attack can happen when visiting otherwise trustworthy websites. Sadly, the website owner is usually unaware that any of this is even going on.
8 Public WiFi

Do not trust the WiFi at that coffee shop or airport you frequent, as you never know if an evil hacker is parading around as a WiFi access point, hoping you connect and try to log into your bank, for example. They could also be sniffing all the traffic on the otherwise normal WiFi access point, scanning your PC for vulnerabilities, and more. Always use a VPN if you need to use free WiFi, use a firewall on your system, and keep everything up to date.[1]
7 Phishing

Be careful what you open or click on in your email! Hackers have gotten very good at disguising fake emails containing malicious attachments, or links to malicious websites designed to compromise your computer. They can even make these emails appear to come from trusted sources, such as your bank.
There is even something called “spear phishing,” which is when a hacker targets you specifically in order to entice you to open a file or click a link. Perhaps the hacker learned enough about you from your public Facebook page to create an email that successfully might trick you. This type of social engineering attack is one of the most popular because it often works.
Keep in mind that a bank or most reputable websites will never ask you to click a link and log in (unless it’s a password reset email), so if you do click such a link, double check that you are in the right place before you enter your login credentials.
As for email attachments, never open anything unless you were expecting it and it comes from someone you know.[2]
6 Reused Passwords

You should always use a unique password for every website account you have. Don’t log into Facebook with the same password you use for your bank, for example. If one website account gets compromised, as happens quite often these days, a hacker that gains your username/password can go try that combination on any other website.
The more frequently you use the same password in multiple places, the greater the chances that multiple accounts get compromised. To aid in the daunting task of using a unique password for every website, employ the use of a password manager, of which there are many ranging from free to yearly subscriptions.[3]
10 Surprising Things Vulnerable To Hackers
5 Malware
Potentially coming from multiple sources, it doesn’t just serve pop-up windows or annoy you about installing antivirus software, it can turn your computer into a ‘zombie’ that can be woken up when a hacker decides to use it. In many cases, a hacker would control a ‘botnet’ made up of thousands of zombies to launch attacks on a person, company, government, or website. Suddenly your computer is complicit in that effort!
Don’t download software from untrusted locations, and do keep your antivirus up to date (this is becoming a recurring theme, isn’t it?)
4 Unsafe Thumb Drives/Media

Unless you bought it and know exactly what is on it, never plug an unknown USB drive into your computer. This goes for SD cards, CDs and DVDs too. Malicious software can run automatically to infect your machine, sometimes without you ever knowing it.
Did you find a USB drive in the parking lot at work, and are dying to know what is on it? Don’t risk it. Always have updated, current antivirus software installed on your computer, even you Mac users, to help prevent this sort of thing.[4]
3 Compromised Ad Networks

One of the best ways for a hacker to serve malware on trusted websites is to compromise the ad networks those websites use to show ads. This has happened to many a trusted website, including some major news outlets, and usually spells out disaster for people who visit them if malicious ads are being served up.
While controversial, the best way to prevent this is to use an ad-blocker for your web browser. Ad-blockers do prevent websites from earning revenue by serving up legitimate ads when you visit them, but they also prevent you from being hacked when that website’s ads get compromised by hackers.[5]
2 Your Outdated Computer

Still using Windows XP? Unplug it and back away from the computer. It is now highly vulnerable and no longer gets updated by Microsoft. If you don’t keep your computer’s operating system up to date, as well as all the software installed on it, you can suffer from being hacked quite easily, often through one of the other mechanisms in this list.
As annoying as it can be to install updates and reboot, it is vital to remaining safe online.[6]
1 Hotel Computers/Kiosks

Never trust the computers in your hotel’s “business center” if you need to log in to anything online, including your bank or your webmail. The “business” could end up getting your accounts compromised quite easily.
You never know what might be lurking on these shared public computers because you never know who used them before you, and chances are that the hotel staff doesn’t either.[7]
Top 10 Notorious Black Hat Hackers








