 Mysteries
Mysteries  Mysteries
Mysteries  History
History 10 Surprising Stories About the Texas Rangers
 Humans
Humans 10 Philosophers Who Were Driven Mad by Their Own Theories
 Miscellaneous
Miscellaneous 10 Video-Game-Worthy Weapons and Armors from History
 Weird Stuff
Weird Stuff 10 Psychics Who Accurately Predicted Wartime Events
 The Arts
The Arts 10 Pieces of Art Inspired by a Broken Heart
 Health
Health 10 Science Fiction-Sounding New Medical Treatments
 History
History 10 Surprising Facts About the Father of Submarine Warfare
 Space
Space Ten Astonishing New Insights into Alien Worlds
 Weird Stuff
Weird Stuff 10 Bizarre Summer Solstice Rituals Still Practiced Today
 Mysteries
Mysteries Top 10 Haunting Facts About the Ghost Ship MV Alta
 History
History 10 Surprising Stories About the Texas Rangers
 Humans
Humans 10 Philosophers Who Were Driven Mad by Their Own Theories
Who's Behind Listverse?

Jamie Frater
Head Editor
Jamie founded Listverse due to an insatiable desire to share fascinating, obscure, and bizarre facts. He has been a guest speaker on numerous national radio and television stations and is a five time published author.
More About Us Miscellaneous
Miscellaneous 10 Video-Game-Worthy Weapons and Armors from History
 Weird Stuff
Weird Stuff 10 Psychics Who Accurately Predicted Wartime Events
 The Arts
The Arts 10 Pieces of Art Inspired by a Broken Heart
 Health
Health 10 Science Fiction-Sounding New Medical Treatments
 History
History 10 Surprising Facts About the Father of Submarine Warfare
 Space
Space Ten Astonishing New Insights into Alien Worlds
 Weird Stuff
Weird Stuff 10 Bizarre Summer Solstice Rituals Still Practiced Today
10 Surprising Things Vulnerable To Hackers
With technology taking over more of our daily lives, an increasing number of things are vulnerable to hacking. It’s a problem that will only get worse because many companies offer lax protection or ignore cybersecurity altogether. Anything with a microchip is at risk, even some things you wouldn’t expect.
10 Any Device In Your Body
Your heart belongs to you . . . unless you have a pacemaker. Then it can be hacked. In fact, any medical device in your body that is connected to the Internet is vulnerable. It’s not a matter of speculation, either, because it’s already happened.
At the 2011 Black Hat Technical Security Conference, security expert Jerome Radcliffe hacked his own insulin pump to demonstrate the device’s vulnerability. He remotely disrupted the wireless signals sent to his pump, swapped the data being captured about his condition with fake data, and sent it back. Radcliffe obviously didn’t tamper with his device enough to put his health at risk, but changing the dose of insulin could have easily put him in a coma or even killed him.
Radcliffe is not the only person doing this kind of research. Barnaby Jack, a researcher for McAfee, found a way to scan for and compromise any pumps within a range of 90 meters (300 ft) using their wireless links.
The same thing is possible with heart defibrillators. When they are first implanted, the devices are tested using a radio signal that turns the defibrillator on and off. Researchers found that it was also possible to capture the signal and rebroadcast it to turn a defibrillator on and off remotely.
9 Toilets
A top-of-the-line Japanese toilet has been found to be extremely vulnerable to even the most basic attempt at hacking. Advertised in the US as defining “toilet innovation,” Satis toilets use a smartphone app called “My Satis” to control them. But in a mind-numbingly obvious oversight, the app uses the same Bluetooth PIN to link to every toilet.
So what can a toilet hacker do to you? The most basic hack would cause your toilet to flush constantly and send your water bill sky-high. The toilet also has an air purifier, automatic lid, in-bowl spotlight, and built-in sound module to cover up the sounds of doing your business. If a hacker catches you on the commode, they could manipulate these features, which Satis has admitted may cause “discomfort and distress to [the] user” as well as increase your electricity bill. However, the toilet costs $4,000, so anyone who can afford one can probably also pay skyrocketing water and electricity bills.
But the worst hack on a Satis toilet might just be the two-nozzle bidet spray, which shoots jets of water at you in lieu of using toilet paper. At best, it would be inconvenient to have this happen unexpectedly. At worst, it’s embarrassing to know that someone is invading one of your most private moments.
8 The Emergency Broadcast System
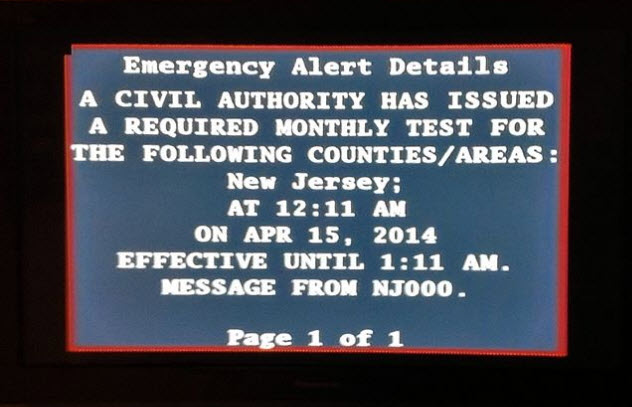
Montana’s Emergency Alert System once warned its television viewers that “the bodies of the dead are rising from their graves and attacking the living.” The alert was quickly pulled, and the TV station apologized, explaining that their Emergency Alert System had been hacked.
The prank happened in several other places, too, including one in Michigan during an airing of the children’s show Barney. These were the first hacks of the system because it used to be telephone-based. But within a year of launching a web-based system, hackers saw it as a potential target and broke in.
The pranks proved to be harmless, but the system’s vulnerabilities became public knowledge, especially the fact that several models of Emergency Alert System decoders could be easily hijacked. The zombie apocalypse messages were clearly fakes, but more serious messages with dangerous consequences could easily be broadcast to the public. If false alarms were raised enough times, people might even start to ignore them.
Although the company that made the systems had fixed another flaw to stop hackers, the zombie attack message proved that the systems were still susceptible to human error. Many users forgot to change the default passwords, which was how these breaches happened.
7 Almost Everything At Your Hospital

If you’re in the hospital and there’s an Ethernet cable connecting your equipment to the Internet, that equipment is probably extremely vulnerable to hackers. By searching for simple medical terms on Shodan, a search engine for finding Internet-connected devices, researchers were able to locate machines like MRIs, X-ray scanners, and infusion pumps. In fact, just about anything connected to the Internet in the hospital is at risk, whether by design or configuration error. But what the researchers discovered next was even more startling.
Much of the medical equipment was using the same default passwords throughout different models of the devices. In some cases, manufacturers warned their customers that changing default passwords could make the equipment ineligible for support because the support teams use those passwords for servicing purposes. Cybersecurity experts were easily able to make a cloud of most frequent logins and passwords.
To see how many medical devices were compromised, the researchers set up 10 computers that looked like medical systems to lure hackers. They got 55 successful login attempts, 24 exploits, and 299 malware samples.
The hacks can be used for many things. The scariest would be hackers changing medication dosages remotely, which a few patients have already done on-site. Medical records can be altered, which could lead to patients not receiving the proper treatments. Phishing scams would also be easy to craft. Even using internal health provider networks, the researchers were able to access host names, descriptions and locations of equipment, and the physicians assigned to that equipment.
6 Smart Homes
With the smart home industry in its infancy, a lot of the technology just isn’t up to modern cybersecurity standards. In 2015, a security company tested 16 home automation devices and found only one that they couldn’t easily hack. Things like cameras and thermostats lacked the most basic security measures. It’s worrisome for a number of reasons, including cybercriminals using your patterns of behavior to put your safety at risk.
Homeowners using smartphone apps to control their houses from a distance are especially vulnerable to breaking and entering. One Forbes reporter found that a string of keywords that could be crawled by search engines led to the systems of some residents winding up on the Internet’s search results for anyone to control.
A hacker could easily open the person’s garage door to enter their home. The particular model that allowed this exploit was recalled, but other systems had a security oversight that let them be controlled by anyone on the same Wi-Fi network.
The vulnerabilities extended to just about every home device connected wirelessly. One hacker took control of a family’s baby monitor and started shouting expletives at their two-year-old daughter. It didn’t bother the girl much since she was deaf, but other cases of hacked baby monitors have not been so benign.
5 Gas Pumps

Fearing that gas pumps connected to the Internet could be vulnerable to hacking, cybersecurity researchers set up fake gas pumps to lure hackers. The researchers quickly found that their fears were justified. Within six months, there were 23 different attacks.
Studies show that there are already gas pumps that have been modified by hackers. So far, the changes haven’t been harmful, but they could have been. The research turned up two denial-of-service attacks that could have disrupted inventory and led to shortages. Four others were pump modifications, and 12 were identification changes, which could alter pump names and cause the wrong type of fuel to flow into a tank. In some instances, this could ruin a car’s engine.
The honeypots (fake devices) were set up all over the world, proving that it’s a global problem. Many automated tank gauges (ATGs)—which monitor volume, temperature, and water content of underground gas tanks—don’t have passwords.
With the documentation of ATGs available to anyone online, it’s a simple task to invade and disrupt service. The researchers found that the US and Jordan suffered the most honeypot attacks and believe that the Syrian Electronic Army or Iranian Dark Coder could be behind them.
4 Airport Security

Cybersecurity experts are now warning that an airport’s security network could be completely shut down by hackers. Many of the security machines, such as X-ray scanners and itemisers (explosive detectors), have passwords built into their software. Anyone with the username and password could log on and get access to an airport network. Hackers could also manipulate an X-ray machine to hide weapons or steal data on how to bypass security. Itemisers could likewise be compromised.
After the vulnerability was discovered, the Department of Homeland Security issued a warning about the passwords, but experts warn that some airports may have already been breached. In 2015, a security firm claimed that an Iranian group hacked supposedly secure information from several airports. The firm warned that anyone with a copy of an airport’s emergency plan could find ways to overcome it. They worry about the potential risk of terrorism and how a group could use that knowledge to plan an attack.
Groups like ISIS have already hacked the website of Hobart International Airport, defacing it with a statement supporting the group. Polish airline LOT was forced to cancel or delay flights after their computers that issued flight plans were hit with a distributed denial-of-service attack.
3 Airplanes

Even if airport security fixes its vulnerabilities, an actual airplane can still be hacked. To search for backdoors, one researcher bought original parts from an aviation supplier to simulate the data exchange between passenger jets and air traffic controllers. He demonstrated that security is so weak that a smartphone equipped with a self-made app is enough to gain access to a variety of aircraft systems. Terrorists don’t need a bomb to crash an airplane because they can take control of the plane’s steering and direct it into the nearest building.
IT expert Chris Roberts claims to have penetrated the entertainment system of a passenger jet and manipulated its engines during a flight. He did so by hooking up his laptop to the Seat Electronic Box, which is usually under each passenger seat. Through that, he claims he was able to enter the command “CLB” to make the engines react to a “climb” command.
With newer planes increasingly reliant on integrated systems, the problem is likely to become worse until airplane manufacturers address the problems.
2 Your Car
In 2015, researchers used a “zero-day exploit” to target a Jeep Cherokee and give them wireless control of the vehicle while it was on the road. The exploit sent commands though the Jeep’s entertainment system into its dashboard functions.
The Jeep’s driver, a reporter who volunteered to be part of the experiment, was driving down the road at about 115 kilometers per hour (70 mph) when the researchers set the cooling to maximum, changed the radio station, and began blasting music at full volume. The windshield wipers turned on, and wiper fluid started spraying, blurring the glass.
Though the driver manually tried to stop all of this, there was nothing he could do. The researchers even playfully put their image on the car’s digital display and shouted, “You’re doomed!” Then they cut the transmission, effectively killing the vehicle and forcing it off the road.
All of this happened when the reporter was on a highway. Though he knew in advance what was going to happen, it was still a nerve-racking experience for him. The researchers warn that it could have been far worse. Later in the test, they cut the brakes, forcing the reporter off the road and into a ditch. They could have also made the Jeep stop suddenly, leading to an accident. They say they haven’t mastered steering control yet, but they’re working on it.
1 Unopened PCs

A new PC should be safe from hackers, but some Chinese computers were sold with preinstalled malware. The malware was embedded into counterfeit versions of the Windows OS. It was being used to spy on users and conduct denial-of-service attacks.
Microsoft’s investigation of the supply chain found that the command-and-control system of these computers was infected with malware called “Nitol.” The malware spread via removable drives, so it’s estimated that millions of computers were infected. When investigators purchased 20 laptops and desktops from “PC malls” throughout China, each one had a counterfeit copy of Windows. Three had inactive malware, and the fourth had a live piece of malware that became active as soon as the PC was connected to the Internet.
The investigators believe that the computers were infected sometime after they left the factory. The Nitol botnet was controlled through the domain 3322.org, which contained more than 500 strains of malware. Microsoft shut down the malware and took control of the domain. It is now allowing legitimate traffic from the site’s subdomains.
Nathan keeps a Japan blog where he writes about the sights, expat life, and finds Japanese culture in everyday items. You can also find him on Facebook and Twitter.







