 History
History  History
History  Health
Health 10 Everyday Activities That Secretly Alter Consciousness
 History
History Top 10 Historical Disasters Caused by Someone Calling in Sick
 Animals
Animals 10 New Shark Secrets That Recently Dropped
 Movies and TV
Movies and TV 10 Forgotten Realities of Early Live Television Broadcasts
 Technology
Technology 10 Stopgap Technologies That Became Industry Standards
 Weird Stuff
Weird Stuff 10 Wild Facts About Taxidermy That You Probably Didn’t Know
 Travel
Travel 10 Beautiful Travel Destinations (That Will Kill You)
 Miscellaneous
Miscellaneous 10 Modern Marriage Rituals Born from Corporate Branding
 Weird Stuff
Weird Stuff Ten Bizarre Visions of 2026 from Fiction
 History
History 10 “Modern” Problems with Surprising Historical Analogs
 Health
Health 10 Everyday Activities That Secretly Alter Consciousness
 History
History Top 10 Historical Disasters Caused by Someone Calling in Sick
Who's Behind Listverse?

Jamie Frater
Head Editor
Jamie founded Listverse due to an insatiable desire to share fascinating, obscure, and bizarre facts. He has been a guest speaker on numerous national radio and television stations and is a five time published author.
More About Us Animals
Animals 10 New Shark Secrets That Recently Dropped
 Movies and TV
Movies and TV 10 Forgotten Realities of Early Live Television Broadcasts
 Technology
Technology 10 Stopgap Technologies That Became Industry Standards
 Weird Stuff
Weird Stuff 10 Wild Facts About Taxidermy That You Probably Didn’t Know
 Travel
Travel 10 Beautiful Travel Destinations (That Will Kill You)
 Miscellaneous
Miscellaneous 10 Modern Marriage Rituals Born from Corporate Branding
 Weird Stuff
Weird Stuff Ten Bizarre Visions of 2026 from Fiction
Top 10 Codes and Ciphers
The need to conceal the meaning of important messages has existed for thousands of years. Over time, people have found increasingly complex ways of encoding their messages as the simpler ways are decoded with greater ease. Contrary to layman-speak, codes and ciphers are not synonymous. A code is where each word in a message is replaced with a code word or symbol, whereas a cipher is where each letter in a message is replaced with a cipher letter or symbol. In fact, when most people say “code,” they are actually referring to ciphers. Ancient scripts and languages have been understood using decoding and deciphering techniques, most famously the Rosetta Stone of Ancient Egypt. In fact, codes and ciphers have determined the outcome of politics and wars throughout history. There are thousands of types of hidden messages, but here we look at only ten as an overview. Several have examples for you to test yourself with.
Steganography is more ancient than codes and ciphers and is the art of hidden writing. For example, a message might be written on paper, coated with wax, and swallowed to conceal it, only to be regurgitated later. Another way is to tattoo the message on the shaved head of a messenger and wait for the hair to regrow to cover up the ink. The best stenography uses innocent everyday objects to carry messages. In England, a once-popular technique was to use a newspaper with tiny dots under letters on the front page indicating which ones should be read to spell out the message. Some people would spell out a message using the first letter of every word or use invisible ink. Rival countries have shrunk writing down so that an entire page of text becomes the size of a pixel which is easily missed by prying eyes. Steganography is best used in conjunction with a code or cipher, as a hidden message always carries the risk of being found.

This is a cipher familiar to many children. Its key is simple: each letter of the alphabet is replaced with the following letter, so A is replaced with B, B is replaced with C, and so on. “ROT1” literally means “rotate 1 letter forward through the alphabet.” The message “I know what you did last summer” would become “J lopx xibu zpv eje mbtu tvnnfs.” This cipher is fun because it is easy to understand and use, but it is equally easy to decipher if the key is used in reverse. This cipher is not suitable for serious use but can be of great amusement for children. Try to decipher the message “XBT JU B DBU J TBX?”!

In transposition ciphers, the letters are rearranged according to some predetermined rule or key. For example, words might be written backward, so that “all the better to see you with” becomes “lla eht retteb to ees uoy htiw.” Another transposition key is to swap every pair of letters, so the previous message becomes “la tl eh eb tt re to es ye uo iw ht.” Such ciphers were used during the First World War and the American Civil War to send sensitive messages. Complex rules of rearrangement can make these ciphers seem very difficult at first. Still, many transposed messages can be deciphered using anagrams or modern computer algorithms, which test thousands of possible transposition keys. To test yourself, try to decipher: THGINYMROTSDNAKRADASAWTI.
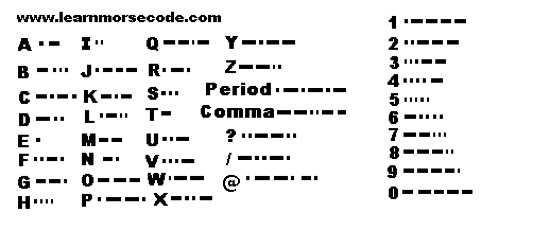
Despite its name, Morse code is not a code but a cipher. Each letter of the alphabet, the digits 0-9, and certain punctuation symbols, are replaced by a sequence of short and long beeps, often called “dots and dashes.” A becomes “•-“, B becomes “-•••” and so on. Unlike most other ciphers, it is not used to conceal messages. Morse code was of great use with the invention of Samuel Morse’s telegraph, which was the first widely-used electric means of sending messages long-distance. It involved laying a long wire between places and running an electric current down the wire. The electric current could be detected by a receiver many kilometers away, and dots and dashes were simulated by turning the current on and off. The telegraph revolutionized media, allowing events in one country to be immediately reported in another. It changed the nature of warfare by allowing instantaneous communication with troops a long distance away. •–• •- •-• •- -••• • •-•• •-•• ••- —
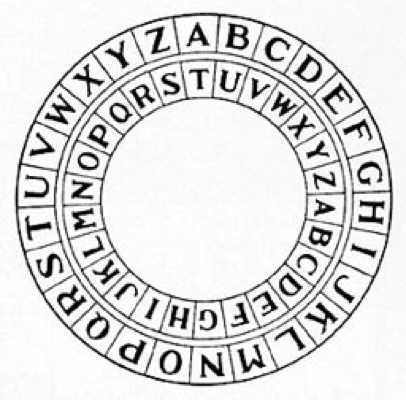
The Caesar shift cipher, named because Julius Caesar himself used it, is actually 26 different ciphers, one for each letter of the alphabet. ROT1 is just one of these ciphers. A person only needs to be told which Caesar cipher was used to decipher a message. For example, if the G cipher is used, then A becomes G, B becomes H, C becomes I, and so on through the alphabet. If the Y cipher is used, then A becomes Y, B becomes Z, C becomes A, and so on. This cipher is the basis for many more complex ciphers, but on its own does not allow great protection of a secret message, as checking 26 different cipher keys does not take a relatively great amount of time. Li bra ghflskhu wklv dqg bra nqrz lw, fods brxu kdqgv.
During the U.S. Civil War, communication on the battlefield was difficult. Although the telegraph was in use, it was not practical on the field as few telegraph lines ran through a battle area. An American telegrapher named Albert Myer developed a new means of communication by waving flags. He used what he knew about communicating with the deaf to create a new system. Myer’s dissertation for his medical degree was titled “A New Sign Language for Deaf Mutes.” Myer “transformed [telegraph] code into a means of personal communication by which words could be spelled by tapping them out upon a person’s cheek or hand.” Stationed in Texas in the mid-1850s as a medical officer, Myer “converted this sign language into the flag and torch signaling system that became known as ‘wig-wag.’”
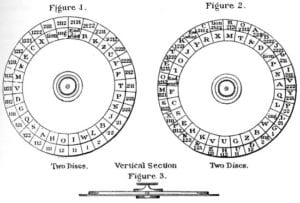
With both the North and South using the same system, encryption was required to protect visual messages from being understood. Most often, a cipher disk was used to encrypt the letters before they were waved. Signalmen needed to place themselves in a visible vantage point that allowed them to signal across great distances. It also gave them an extended view of the surrounding area.
Each letter of the wig-wag alphabet was represented by a certain position or movement of the flag. In wig-wag code, messages were spelled out according to a letter-number code. Each letter of the alphabet was represented by a combination of numbers, and the numbers corresponded to flag movement. A movement to the left of the center meant a “1,” and a movement to the right of center meant a “2.” The letter A, for example, was “11,” which is two movements from the left to the center in a row. Dipping the flag forward one or more times signaled the end of a word, sentence, or message. Try this one: 1122/11/1111/111/211/2222

This cipher is more complex than monoalphabetic substitution. Its key is a word, such as “CHAIR.” The rule of the cipher is similar to that of the Caesar shift cipher, except it changes with every letter according to the keyword. The first letter of a message with the keyword CHAIR would be encoded with the C cipher alphabet, the second with the H cipher alphabet, and it continues like this through the keyword. The keyword is only five letters long, so a C cipher is used again for the sixth letter of the message. The Vigenère cipher was thought to be unbreakable for a long time. To decipher, the length of the keyword is guessed first. If the keyword is guessed to be five letters long, then letters numbered 1, 6, 11, 16, 21, etc., will all correspond to the first letter of the keyword, and letter frequency analysis will decipher them. The decoder then moves to letters 2, 7, 12, 17, and so on. If the keyword is indeed five letters long, this will decode the cipher. If not, another keyword length must be guessed and the process repeated. Eoaqiu hs net hs byg lym tcu smv dot vfv h petrel tw jka.

In a true code, each word is replaced by a codeword or number according to a key. Since many words might be in the message, the key is usually a codebook where someone can look up an English word and find the corresponding codeword, not unlike a dictionary. Just as short messages are difficult to decipher with letter frequency analysis, a code needs to be extraordinarily long before word frequency analysis becomes useful. Hence, codes are harder to decode than ciphers. Many countries have used variants of codes, where each day a new code was used to keep them safe from word frequency analysis. For everyday life, however, codes are slow, and making a codebook is cumbersome. Worse, if the codebook is stolen, then the code is no longer safe, and a new one must be made, taking a tremendous amount of time and effort. As a result, codes are mainly useful to the rich and powerful who can delegate this work to others.

The Enigma code, a very sophisticated cipher, was used during the Second World War by the Germans. It involved an Enigma machine, similar to a typewriter, where pressing a letter would make the cipher letter light up on a screen. The Enigma machine involved several wheels which connected letters with wires, determining which cipher letter would light up. All Enigma machines were identical, and knowing the initial configuration of the wheels inside was the key to enciphering messages. To make things harder, each wheel would rotate after a certain number of letters were typed, so the cipher was continuously changing within a message. German commanders had Enigma machines and would be issued lists of the initial wheel configuration to use for each day so that all the Germans used the same one and could decipher each other’s messages. Even when the Allies procured a copy of the Enigma machine, they could not decipher anything, as there were over one hundred trillion possible wheel configurations to check. The Enigma code was broken by Polish ingenuity and perfected by the British using geniuses and computers. Knowledge of German communications gave the Allies a vital advantage in the war, and from breaking the Enigma code, the ancestor of modern computers was born.
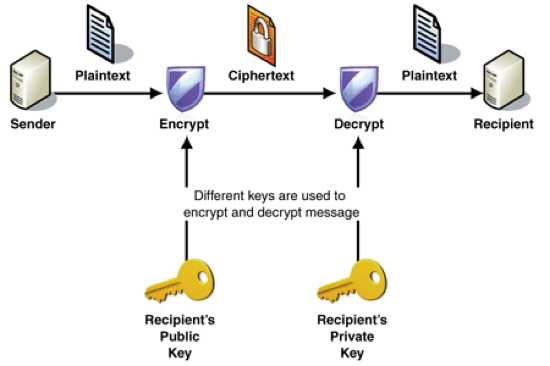
This is the ultimate modern cipher, and it has several variants. This cipher, used worldwide, has two keys: one public and one private. The public key is a large number available to everyone. The number is special in that only two whole numbers (apart from 1 and the number itself) will divide into it perfectly. These two numbers are the private key, and if multiplied together, produce the public key. So the public key might be 1961, and the private key 37 and 53. The public key is used to encipher a message, but it is impossible to decipher without the private key. When you email personal details to a bank or a machine reads your bank card, the details are enciphered this way, and only the bank can access them with their private key. This is so secure that mathematically, it is challenging to find divisors of large numbers. Until recently, to help security, RSA Laboratories gave money to anyone who could find the two divisors of the numbers they gave. For a relatively easy example, once worth USD 1000, try to find the two 50-digit divisors of
1522605027922533360535618378132637429718068114961
380688657908494580122963258952897654000350692006139.








